It’s Back to (Smart) School Time….
August 31, 2022
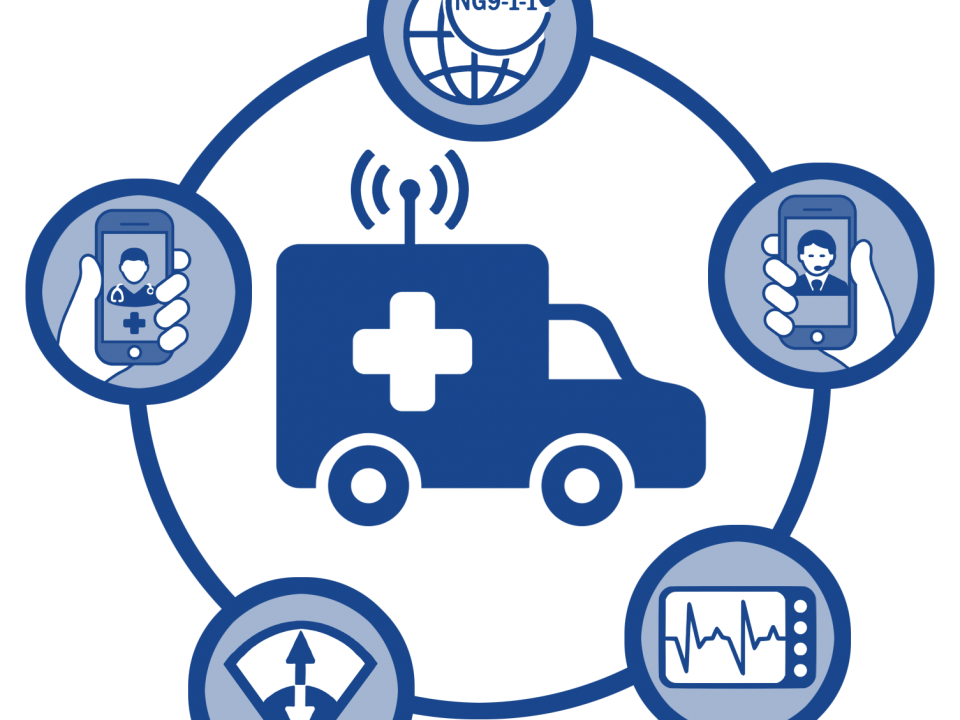
Leveraging Communications Solutions for Disaster Response
October 14, 2022We live in an age where at all times, most of us are within feet of some sort of smart device. Whether it’s a smartphone using GPS to track our location or a smartwatch tracking our movement and providing real time health information, most of us live in a constant state of information gathering and monitoring. Even our TVs are using algorithms to suggest the next best movie or series and our Kindles suggesting what novels we’ll enjoy next. Traffic cameras are monitoring real time movement, photographing license plates and intersections, and storing information in the cloud. Websites use cookies and tracking features to show you an ad for something you mentioned weeks ago…or maybe you didn’t mention it at all and only thought it might be something you need? Whatever the case, if you’re using modern technology, your personal information, habits, schedule, and lifestyle are all being tracked, monitored, and stored for future use.
It’s no wonder that cyber attacks have grown exponentially, targeting financial institutions, government agencies, and medical databases. Large-scale breeches leave thousands, if not millions vulnerable to identity theft, monetary theft, and exposure of protected private information. There are numerous safeguards that have been implemented to avoid these types of vulnerabilities and potentially safeguard your information.
- When possible, use two-step authentication measures. While an attacker may have your email and password, they don’t have your physical device to acquire automatically refreshed codes necessary to complete account access.
- Change passwords frequently and avoid using the same password on various accounts. This can definitely become confusing and at times annoying, but it only takes one known password to unlock multiple accounts leaving your information vulnerable. Do not use identifying information in passwords like your name, company name, school, or names of family members. Avoid using common number sequences as well (e.g., 1,2,3… or 3, 2, 1).
- Social media provides unlimited information to potential hackers. Avoid tagging real-time locations, posting your full birthday, home address, work address, your children’s school or any specific information making it easier to guess passwords.
- Turn off tracking and location settings when applicable. Obviously, you need these services on for GPS apps, ride services, and delivery services. However, it is wise to avoid location sharing in most circumstances.
- Don’t enter personal information on unsecure websites. Look for the lock symbol in the address bar and look for the “s” in the https:// prefix to verify that the website you’re accessing is safe and secure.
- Don’t click links in texts or emails if you can’t verify with absolute accuracy where they originated. Most financial institutions WILL NOT text you a link to verify an account. Whenever there is doubt, find the correct number to your bank and call them directly to verify information and report a potential scam.
There are numerous ways to protect your information from malicious use and these are just some examples. Educate yourself, your family, your coworkers, and employees on the risks associated with improper or lax cyber protections and keep personal information safe and secure. With so much at risk, it’s up to us to keep our information safe and make access as difficult as possible for potential attackers. For more information on protecting your personal information, visit https://www.CISA.gov. If you would like information on cybersecurity grant opportunities, please visit the Department of Homeland Security’s website.